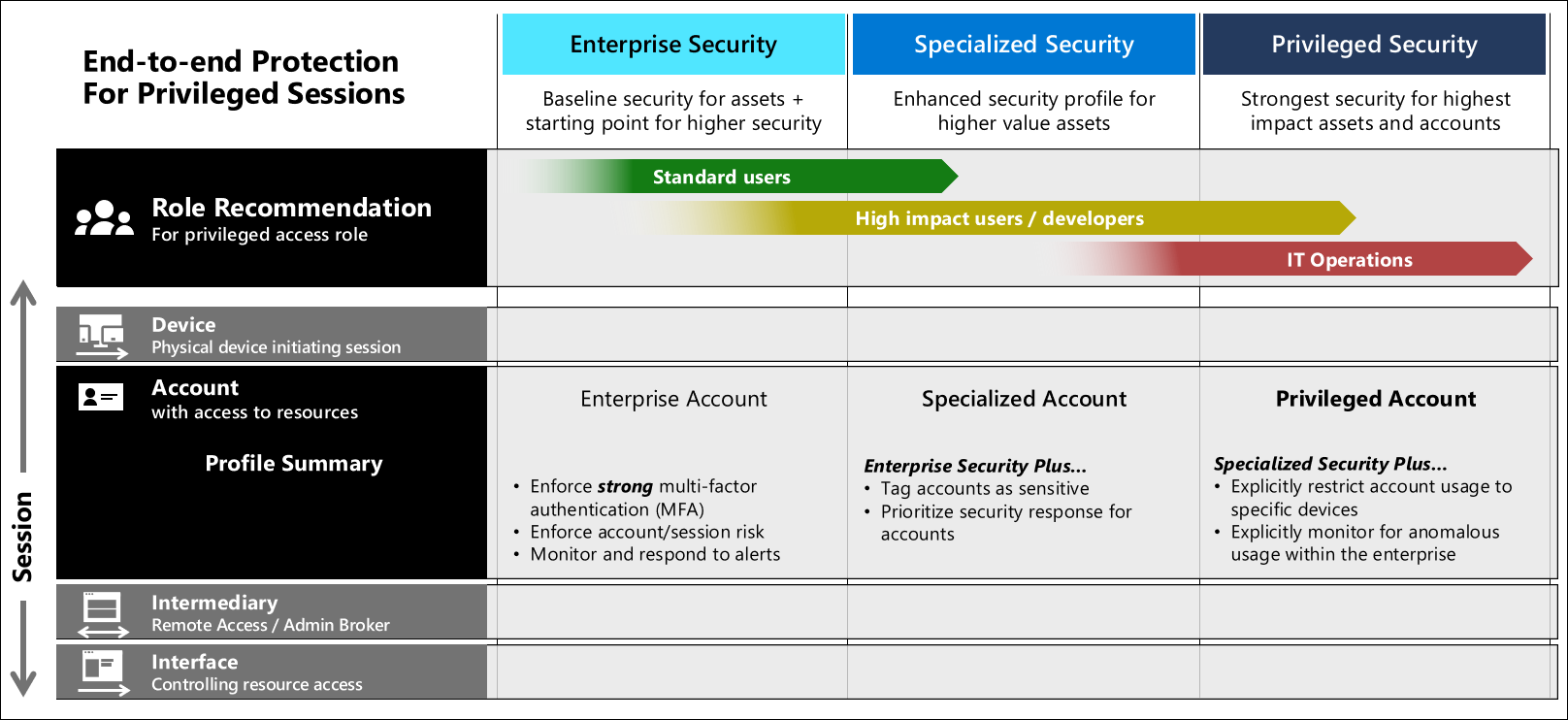
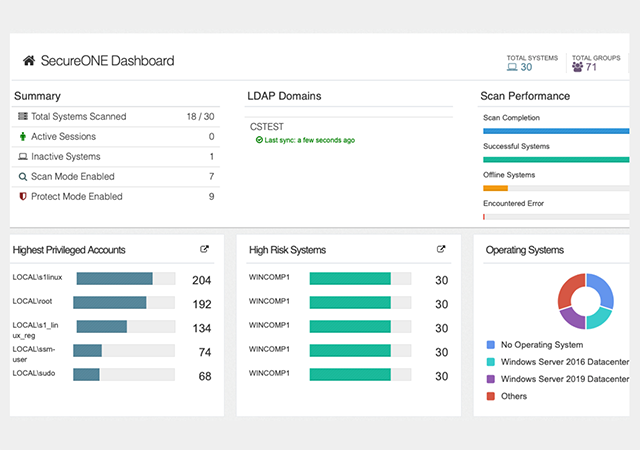
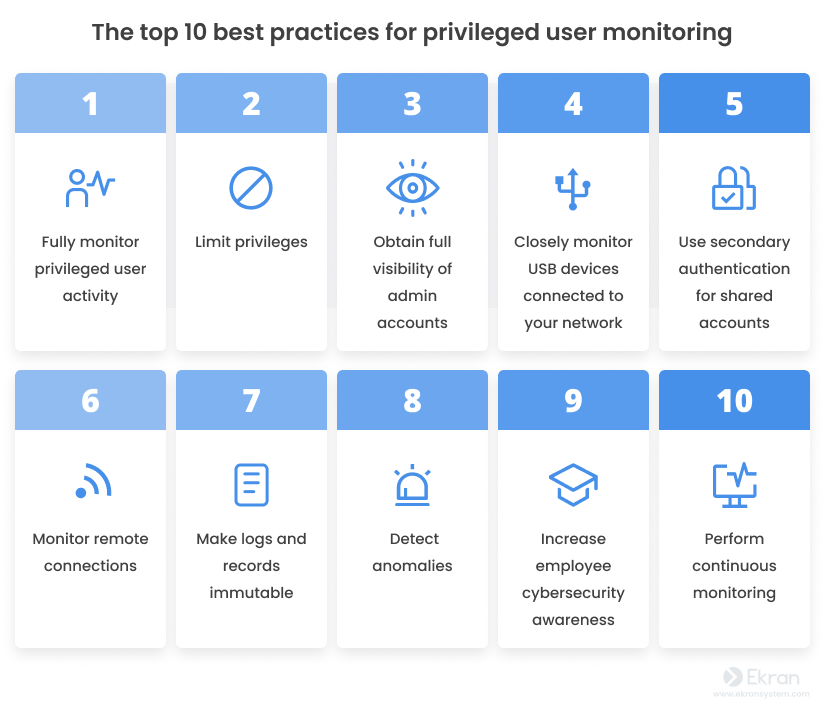
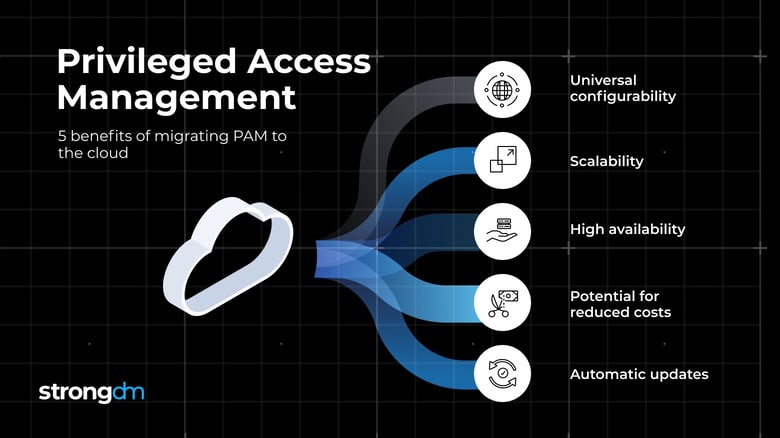
Developing a privileged access strategy Privileged access top, What Is Privileged Access Management PAM top, Best Practices For Monitoring And Controlling Privileged User Access top, Privilege Management CyberRes top, Privileged Identity Playbook top, What is Privileged Access Management PAM and Why It s Important top, First Step to Privileged ID Management Access Check Essential top, Five tips for Privileged Access Management metrics top, Privileged Account Session Management Tips to Deploy PASM top, What is Privileged Access Management PAM top, What is Privileged Access Management PAM top, What Is Cloud PAM Migration Challenges More top, The Ultimate Guide to Privileged Access Management for Windows top, Privileged User Monitoring Top 10 Best Practices to Know top, Privileged Access Management Audit Checklist for 2023 StrongDM top, Privileged Access Management PAM Software from Netwrix top, Securing privileged access accounts Privileged access top, CyberArk Privileged Access Manager CrowdStrike Marketplace top, What Is Privileged Access Management PAM Definition Components top, Privileged User Monitoring Top 10 Best Practices to Know top, Essentials of Privileged Access Management Fortra top, Privileged Access Monitoring for Critical Systems Gurucul top, Privileged User Monitoring Top 10 Best Practices to Know top, What is Privileged Access Management PAM and Why It s Important top, Five tips for Privileged Access Management metrics top, Securing privileged access overview Privileged access top, What is Privileged Access Management PAM top, Privilege Access Management top, Privileged Access Management Why and How to Prioritize It top, What is privileged access management PAM top, What is Privileged Access Management PAM top, What is PAM Security Privileged Access Management Explained top, Privileged access management in Office 365 is now Generally top, Privileged User Monitoring Top 10 Best Practices to Know top, What is Privileged Access Management PAM Delinea top, Product Info: Privileged access monitoring top
.
Privileged access monitoring top